Office 365 users are now being targeted in a pretty convincing looking phishing attack.
Phishing attacks, a common tactic used by cyber criminals to try to trick you into giving them your information, are nothing new. In fact, it’s likely if your company has already been targeted by phishing (and if you haven’t been, it’s a matter of when – not if) and it’s getting harder and harder to spot the malicious emails.
The Office 365 phishing attack is a perfect example. The email appears to be an automated alert email from Microsoft saying the user’s Office 365 account has been suspended and asks them to sign in to reactivate your account. While the email does look realistic, there are some major red flags.
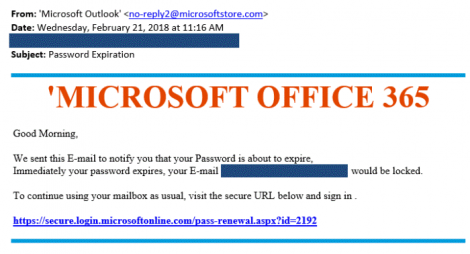
- The From address was not from a Microsoft domain. Alerts from Microsoft will come from an @email.microsoftonline.com address.
- This is meant to scare you. It’s to try to get you to click and log in to the fake sign in screen before having a chance to think about it too much.
- They are attempting to get you to sign in. This will direct you to the fake sign in screen.
- You can’t see it here, but if you hover over the link, it doesn’t direct you to Office 365. It directs you to a non-Microsoft site.
- The privacy and legal links are just text – not actual links. Real Microsoft emails will actually link to the legal information on their site.
If you were to click on the link in the fake email, you’d be taken to a pretty convincing looking Office 365 log in page. But it has it’s own red flags:
- This is not a Microsoft.com domain. This is your biggest and most important red flag. Always check the URL before you log in to any site to make sure you’re actually on the site you think you’re on.
- Company names do not appear on the real Outlook Web App page.
- These radio buttons are meant to scare you. These do not appear as options on the real Outlook Web App page.
- The email address is pre-filled in and cannot be changed.
- This is the only area you can input data. They are attempting to steal your password.
Once you put your password in, it redirects you to a Google doc. At that point, it’s pretty easy to figure out that something is wrong. But before that, you may not know.
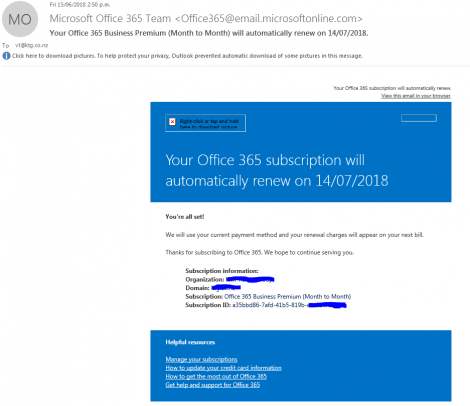
It’s easy for us to spot these red flags, because we’re an IT company and a Microsoft partner who deals heavily with Office 365. We think about this all the time. We know the warning signs for phishing email and know what real Microsoft emails look like. For reference, here is a real Microsoft email:
There is an important thing to notice here: While this alert email has a similar message as the fake alert, it has specific account information and gives a reason for the email, rather than just saying the account is suspended or deleted with no explanation.
But for the average user, this attack would be pretty easy to fall for. Knowing the warning signs of a phishing email is incredibly important as these attacks become more and more common.
If you have entered your email in a log in screen and gotten redirected to something like a Google Doc (or anything else you aren’t expecting), it’s likely you’ve fallen victim to a phishing attack. You’ll need to change your password immediately (and the password for any account that uses the same log in information) and contact your IT company to help you make sure attacker is out of your system.
If you’re ever suspicious about an email or something just doesn’t feel right, don’t click on anything and don’t enter your information into a sign in screen that comes up if you have already clicked.
The easiest way to check these emails is as follows;
- Move the email to your “Junk” Folder. – this will remove the pictures and show you exactly where the links are pointed to. It will also disable the ability to open them by clicking on them.
- You can do this by right–clicking on the message and choosing Junk, then “block sender” –
- this can be undone if it is legitimate. In your “Junk Email” folder you can right-click any email message and choose Junk, then “Not Junk”
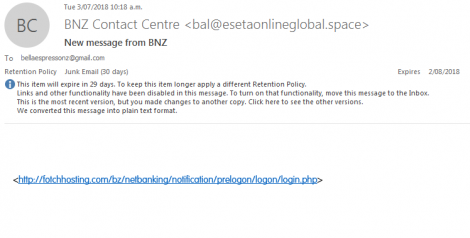
Example: here’s what a scam looks like in my inbox;
All I did was move it to my junk folder, now it looks like this;
As you can clearly see – Nothing to do with BNZ, but trying to get your banking login details.
If you are still unsure about the legitimacy of an email, reach out to your IT company if your suspicious.
It’s better to take the extra few minutes to check than to fall victim to an attack.