Dubbed “Bad Rabbit,” the virus is the latest example of cyber criminals using ransomware to extort cash – here’s everything you need to know.
What is the Bad Rabbit ransomware attack?
Bad Rabbit is a strain of ransomware.
It is believed to be behind the trouble and has spread to Russia, Ukraine, Turkey and Germany.
A message will pop up on users’ screens telling them their computer had been locked and they must pay £280 in Bitcoin to regain access.
Russia has been hit hardest but computers in Turkey and Germany are also reported to be affected.
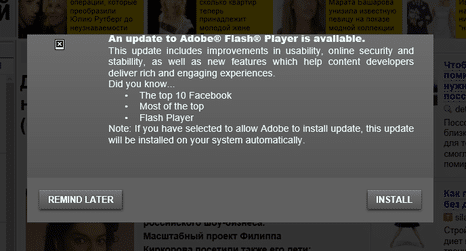
It spreads via a fake Flash update on compromised websites
The main way Bad Rabbit spreads is drive-by downloads on hacked websites. No exploits are used, rather visitors to compromised websites — some of which have been compromised since June- are told that they need to install a Flash update. Of course, this is no Flash update, but a dropper for the malicious install.
How does the malware work?
Bad Rabbit infects a network when one person inadvertently runs a fake Adobe Flash Player installer that has been manipulated to look like the real deal.
After infecting one machine in a network – one computer in an office, for example – Bad Rabbit can find any login details stored on the machine which it uses to spread to others, security researchers have claimed.
Similarly to WannaCry, Bad Rabbit encrypts Windows files, video and audio.
The user receives a message that states: “Oops! Your files have been encrypted.
“If you see this text, your files are no longer accessible.”
The malware is locking users out and demanding money cash.
It can spread laterally across networks…
Much like Petya, Bad Rabbit comes with a potent trick up its sleeve in that it contains an SMB component which allows it to move laterally across an infected network and propagate without user interaction.
What aids Bad Rabbit’s ability to spread is a list of simple username and password combinations which it can exploit to brute-force its way across networks. The weak passwords list consists of a number of the usual suspects for weak passwords such as simple number combinations and ‘password’.
But security experts are warning people not to cough up.
The malware also appears to be using an encryption scheme that prevented analysts from deciphering the malicious code.
It goes by the code-name “Bad Rabbit” but needed to be analysed further.
It’s currently unclear if infected computers can be fully restored.
Yet there are ways to protect yourself from the cyber attack. Ensure your machine is fully backed up. This is almost the only certain way to get out of a Ransomware attack.
If you are unsure if you are protected, ask one of the team at Wizard IT.